 Automotive network security layers and threats
Automotive network security layers and threats
With the upcoming connected vehicles, there is the possibility of many attacks on the vehicle for various intentions. In most cases, an attack starts at the user interaction applications and then spreads inside the vehicle through the network to reach other ECUs deep inside. Attackers can steal personal information by exploiting vulnerabilities in applications. More damage is caused when an attacker manages to pass through the vehicle network to reach critical ECUs. The deeper the attacker can reach into the network, the more damage can be caused.
 Fig 1. Typical EE architecture with High Performance controllers and Ethernet
Fig 1. Typical EE architecture with High Performance controllers and Ethernet
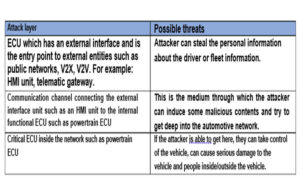
In general, we can classify that attacks on the vehicle network can be under one of three layers.
The connected vehicle offers various interfaces, so it is very important that we secure all the interfaces with all security measures required; otherwise, this will create vulnerability so that the attacker can enter the vehicle networks through these vulnerabilities. By exploiting vulnerabilities, the attacker can get some insight into personal data available at the interface unit.
The communication channels, however, play a very important role in averting a major catastrophe. To gain the remote control of the vehicle or fleet, the attacker needs to gain access to the communication channel. In upcoming E/E architecture, the Ethernet is one of the most important communication channels, and it is quite important to secure this channel and gateways in order to stop the attacker reaching the inside ECUs.
UN R155 Annex 5 [1] section 4.3.2 briefly mentions threats to vehicles regarding their communication channels. The next section provides insight into potential cyber attacks on the vehicle through communication channels.
Cybersecurity threats to vehicles regarding their communication channels
 Man-in-the-middle attack
Man-in-the-middle attack
An MITM attack involves data interception or manipulation of communications between two communication partners such as, for instance, the vehicle application and the external source. The attacker motivation can be to steal personal data or to misguide the vehicle application.
In MITM attacks on the vehicles, attackers intercept legitimate traffic between networks (infotainment & cluster applications accessing external networks) and external data sources such as clouds or public networks. These eavesdropping attacks usually happen due to weak security protocols that allow bad actors to obtain user credentials, hijack user sessions, and steal data (personal information, for example) in real-time transactions.
Replay attack
A replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. The added danger of replay attacks is that a hacker doesn’t even need advanced skills to decrypt a message after capturing it from the network. The attack could be successful simply by resending the whole message.
Malicious triggering of vehicle behavior attacks
In this case the attacker gets the control of the vehicle network by acting as a node; clever attackers use privilege escalation to expand their reach within the target system or network. In horizontal attacks, they gain access to adjacent systems; in vertical attacks, they gain higher privileges within the same system.
The attack is usually made through the infotainment & cluster applications or telematic gateway and moves inside the network to damage other applications within the network. For example, sensor-to-engine messages can be manipulated there by triggering malicious vehicle behavior.
This kind of attack can be dangerous to persons in the vehicle or road users.
False-driver information attacks
In this case the attacker tries to exploit the loopholes in the applications and manipulate the messages that are displayed on the screen. The information that the driver gets on the dashboard might lead to confusion for the driver about vehicle parameters.
Here the main motivation of the attacker can be to demand ransom.
Denial-of-service attack
This can be a scenario where the vehicle applications use client-server techniques. The server provides useful information for different vehicle entities. The attacker jams the server by acting as client application, thereby blocking access of vital server information to other client applications. This can hinder the vehicle applications of especially autonomous or semi-autonomous vehicles.
A malicious actor deploys networks of botnets (large networks of malware-compromised devices) to direct high volumes of false traffic at the vehicle network. This fraudulent traffic overwhelms servers, prevents the legitimate entity from accessing an application, and may cause the unavailability of the server information to the clients. This could lead to trouble in the autonomous vehicles. A DoS attack can cripple a vehicle’s entire network infrastructure.
Here the attacker’s motivation could be a ransom demand.
Black-hole attack
In a black-hole attack, a malicious node uses its routing protocol in order to publicize itself for having the shortest route to the destination node. This aggressive node publicizes its availability of fresh routes regardless of checking its routing table.
In this attack, the attacker node always has the accessibility in replying to the route request to adapt the data packet and drop it.
In a protocol based on flooding, the malicious node reply will be received by the requesting node before the reception of reply from any actual node; therefore, a malicious and faked route will be created. When this route is set up, it’s now depending on the node whether to drop the packets or forward them to an unknown address.
Sybil attack
A sybil attack is a type of attack seen in peer-to-peer networks in which an ECU in the network operates multiple identities actively at the same time and undermines the authority/power in reputation systems.
The main aim of this attack is to gain major influence in the network, to carry out illegal (with respect to rules and laws set in the network) actions in the system. A single entity (an ECU) has the capability to create and operate multiple identities (user accounts, IP address-based accounts). To outside observers, these multiple fake identities appear to be real, unique identities.
Enhancing security at the Ethernet communication channel and gateways
Securing the Ethernet channel and gateways makes it harder for the attacker to carry out the attacks discussed in the first section. Most attack efforts are filtered out at this level and can safeguard the critical ECUs.
In the modern electrical architectures, the Ethernet forms the major elements of the electrical architecture. The Ethernet is the main channel that connects the external communication ECU to the other domain ECU such as powertrain and body control modules.
The Ethernet channel is the potential medium where the attacker has to pass through to gain control of the other ECU in the network. Increasing Ethernet security leads to a more secure architecture as well. The Ethernet is an important medium to stop the hacker attacking core functions of the ECUs.
 ECUs with Ethernet being the main element of the network, secure Ethernet can provide some degree of protection against cyber attacks discussed in the previous section. By securing the Ethernet, the attacks can be prevented from reaching other parts of the network, thereby increasing the overall security of the automotive network.
ECUs with Ethernet being the main element of the network, secure Ethernet can provide some degree of protection against cyber attacks discussed in the previous section. By securing the Ethernet, the attacks can be prevented from reaching other parts of the network, thereby increasing the overall security of the automotive network.
Secure gateways
Using Ethernet switch hardening and IDS
In the zonal architecture, HPC nodes usually communicate with the other nodes over protocols such as SOME/IP. MITM attacks exploit the SOME/IP protocol. The scenario involves an adversary hijacking a connection between two applications on two separate ECUs, enabling the attacking ECU to eavesdrop on communications between the applications and manipulate the data sent. The type of mitigation methods that can be used depends on the network properties, but the use of advanced, automotive-specific security mechanisms are highly recommended in order to prevent attacks such as this one.
Some cases such as SOME/IP-SD traffic are of a multicast nature. So, they cannot be authenticated or encrypted using a standard protocol. The SOME/IP traffic can be authenticated or encrypted, but it will not prevent the attack, as the attacking ECU is sending SOME/IP messages on behalf of its own, after legitimately subscribing to the service.
There are several ways to mitigate this kind of attack, the preferred choice mainly depends on the network properties. In some cases, hardening the switch with proper TCAM rules or VLAN configuration might prevent the attack, but in other cases, it will not be enough. Generally speaking, it is highly recommended to use advanced security mechanisms that will filter the traffic not only based on regular network parameters (MAC addresses, IP addresses, and UDP/TCP ports), but also on automotive network parameters, such as SOME/IP service ID and SOME/IP-SD message type.[2] Sophisticated IDS and IDPS is required to monitor the flow of traffic and to analyze any anomaly. The application can develop sophisticated IDS and can use the Ethernet switch to block the traffic originated for a particular IP if it detects the intrusion.
Firewall
Using firewalls and more powerful IDS/IPS systems, it is possible to separate IP networks with different protection requirements more strictly from each other and monitor them more precisely. By contrast, traditional automotive bus systems, by virtue of being broadcast media, cannot be separated logically – unless an additional physical bus is installed.
For these reasons, established security technologies often make their way into vehicle networks only in a modified form – for example, when VLANs can be used to enhance their fail-safe properties. To this end, the network can be divided into virtual zones with different protection needs, via which the network traffic of safety-relevant components can be identified in real time. If required, the network can then be prioritized or isolated. If a denial-of-service (DoS) attack or faulty component floods the network with packets, they can be stopped at the next switch by means of rate limiting to give precedence to the communication in the prioritized VLAN link to attacks.
Ethernet stack security features
By employing the CIA properties on the communication channel, it offers some degree of protection against the malicious attacks. The Ethernet with its OSI model offers security at various levels. The following table lists security features of the Ethernet at different layers that can help to keep the network secure.
 Table 2: OSI layers and security features
Table 2: OSI layers and security features
SecOC
The Secure On-Board Communication (SecOC) provides functionality necessary to verify the authenticity and freshness of Protocol Data Unit (PDU)-based communication between ECUs within the vehicle architecture. The approach requires both the sending ECU and the receiving ECU to implement a SecOC module.
To protect the authenticity of data packets, the SecOC module specification was released in 2014 as part of AUTOSAR 4.2. The specification is so flexible that SecOC is also suitable for Ethernet/IP-based traffic. SecOC involves adding the authentication and freshness counter value to defend the vehicle against the various cyber attacks.
TLS
The Transport Layer Security (TLS) protocol can be considered for time-uncritical communication with backend systems or test devices. The TLS 1.3 specification offers substantial innovations: with optimizations in how connections are established (zero-RTT handshakes), TLS-secured data can be accommodated in the first packet during the handshake. Additional roundtrip times are no longer required when using TLS. As the use of pre-shared keys could mean that asymmetrical processes are no longer needed, the overhead costs of TLS can be dramatically reduced as well. For the present, however, the focus is on carefully evaluating the possibilities with regard to a potential weakness of the TLS security guarantees.
IPSsec
The IP security (IPSec) is an Internet Engineering Task Force (IETF) standard suite of protocols between two communication points across the IP network that provides data authentication, integrity, and confidentiality. It also defines the encrypted, decrypted, and authenticated packets. The protocols needed for secure key exchange and key management are defined in it.
IP security has the following components:
Authentication Header (AH) – It provides data integrity, authentication, and anti-replay. The anti-replay protection safeguards against the unauthorized transmission of packets.
Encapsulating Security Payload (ESP) – It provides data integrity, encryption, authentication.
IPsec can be used to do the following:
- Application layer data encryption.
- Enabling security for routers sending routing data across the public internet.
- Authentication without encryption, authenticate that data originates from a known sender.
- In case of V2X communication where the publisher is the external entity outside the vehicle, protect network data by setting up circuits using IPSec tunneling in which all data being sent between the two endpoints is encrypted, as with a virtual private network (VPN) connection.
MACsec
Media Access Control Security (MACsec) was introduced in 2006 by IEEE 802.1AE. It operates at the data-link layer (layer 2) and secure point-to-point link. The hop-by-hop encryption enables confidentiality and integrity of data at layer 2.
It encrypts entire Ethernet packets except source and destination MAC addresses on any device-to-device, switch-to-switch, or router-to-switch connection. With MACsec configured, each packet on the wire is encrypted.
With MACsec, it is possible to ensure the following properties of the message:
Confidentiality: MACsec protects our data from unauthorized access. An unauthorized user should not be able to reach the content of data. MACsec provides confidentiality by using strong encryption.
Integrity: Integrity means protecting our data from unauthorized alteration. So, it should have a mechanism to detect the modification of data. MACsec performs an integrity check to prevent data tampering and make sure that data is not modified in transit.
Flexibility: MACsec is flexible as we can enable or disable it on any selective interface on a MACsec-capable device.
These are some of the techniques we can employ within the Ethernet channel which can help prevent many identified cyber-attacks. With upcoming vehicle connectivity, Ethernet security plays a major role in preventing cyber-attacks.
References
[1]. UN R155 document Annex 5: https://unece.org/sites/default/files/2021-03/R155e.pdf
[2]. Hijacking SOME/IP protocol with man-in-the-middle attack: Hijacking SOME/IP Protocol with Man-in-the-Middle Attack – Argus Cyber Security (argus-sec.com)
About the author
 Ganapathi Parameshwar Bhagwath
Ganapathi Parameshwar Bhagwath
Senior Technical Specialist
Elektrobit India Pvt. Ltd
Ganapathi brings over 16 years of experience in Embedded Automotive domain. He holds a Master’s degree in Technology and has a specialization in Automotive Cybersecurity, Automotive Networking, and AUTOSAR. He works with multiple clients in the automotive industry on getting ready for the ISO 21434 standard and the UN R155 regulation. He also works towards building cybersecurity defense mechanism within the automotive domain.
About Elektrobit
Elektrobit is an award-winning and visionary global vendor of embedded and connected software products and services for the automotive industry. A leader in automotive software with over 35 years of serving the industry, Elektrobit’s software powers over five billion devices in more than 600 million vehicles and offers flexible, innovative solutions for car infrastructure software, connectivity & security, automated driving and related tools, and user experience. Elektrobit is a wholly-owned, independently-operated subsidiary of Continental.

